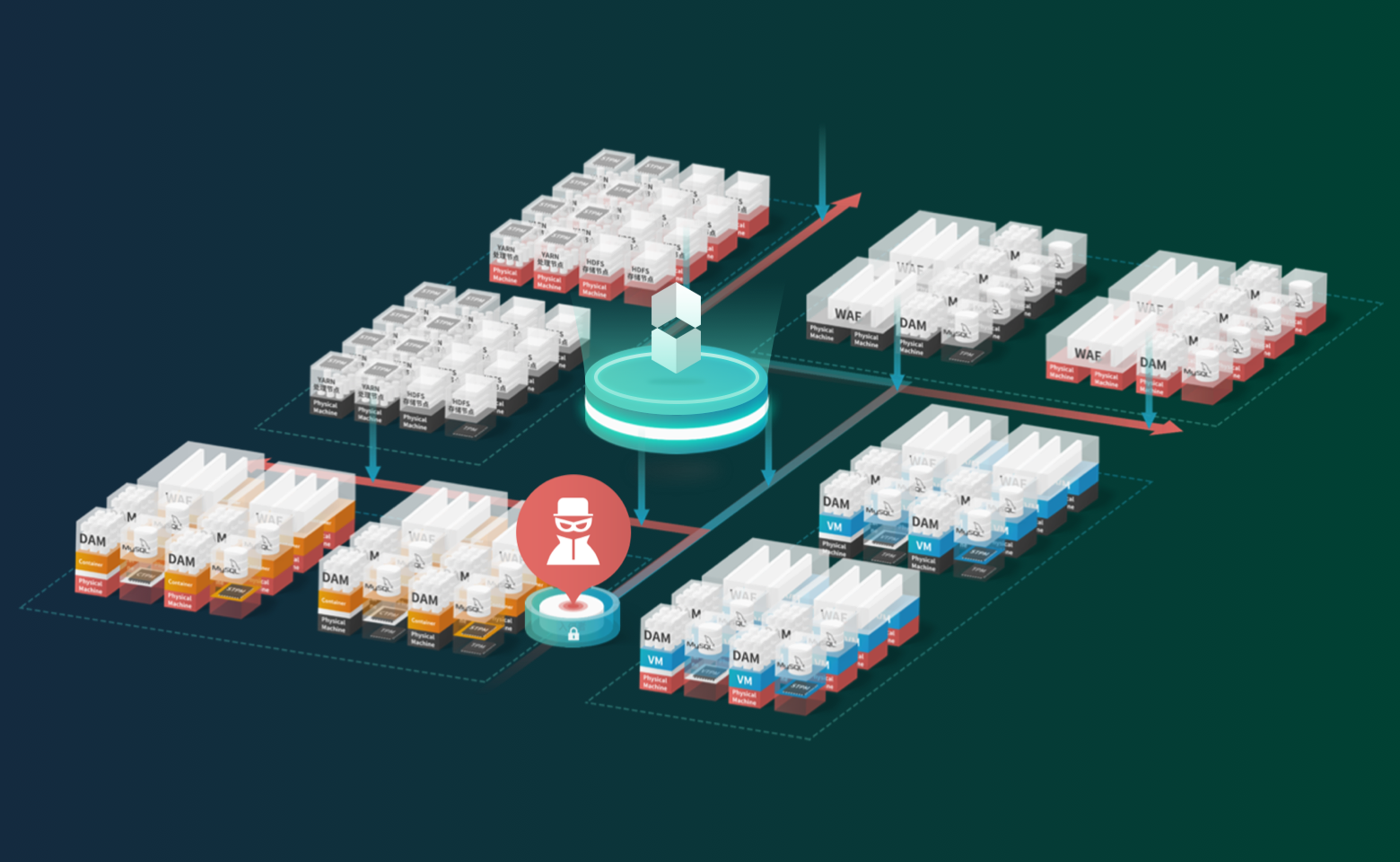
Product Overview
Incorporated the global pioneering trusted computing technology, blockchain technology and artificial intelligence technology, OCTA Innovations develops the Continuous Immune System, a security management platform, to resolve the security problems of hosts under cloud circumstances. Through continuous monitoring and analysis, the Continuous Immune System will automatically generate an executable whitelist for every server to build a self-monitoring active defense certificate system.
Technical characteristics
The system is mainly composed of three modules: "trusted defense, autonomous countermeasure and block chain tamper-proof", forming a complete set of trusted defense system.
Perceives abnormal operation behaviors in 10 seconds.
Detects the abnormal operation behavior by embezzlers quickly according to the behavior portrait of the big data administrator.
Precisely filters abnormal process with extremely low false positive rate.
Captures the most subtle operations by system-level operational behavior analysis.
Detects abnormal process in 1 second.
Filters 100% abnormal process by automated whitelist system layer analysis.
Counters the hacker with ROOT permission by trusted hardware-level monitoring.
Generates the fine-grained whitelist automatically to reduce management complexity.
Blockchain systematic behavior storage certificate, which the tamper-proof achieves the strength of Bitcoin ledger level.
All records are saved incrementally; All changes are recorded and can be traced and verified.
Initiate heterogeneous consensus, which improves the consensus efficiency and enhances the blockchain security.
100-thousand-level TPS (Transactions Per Second), achieves database-level storage efficiency.
Responds immediately and deploy the autonomous countermeasure automatically in 15 seconds.
Anticipates the intruder's attack path, understanding the intrusion better than the intruder.
Counters perceived threats Intelligently and autonomously to assist security operation and maintenance.
The expert system assists the implementation of countermeasures, enhancing defense synergistically.
产品展示
欲了解详情,我们可为您提供详尽的演示
- 八分量持续免疫产品讲解