Overview
Based on the development goal of industrial optimization and digital upgrading, the Industry Factors Data Services Platform fully integrates the industrialized, digitalized and platform-oriented efficiency demands, provides trusted data support for supply chain and industrial finance, and provides effective empowerment of low-cost and high-efficiency capital and resources for enterprises. With the future development trend of industrial digitization and internationalization as the goal, we play the advantages of market aggregation and promote the high efficiency and cluster development of industry.
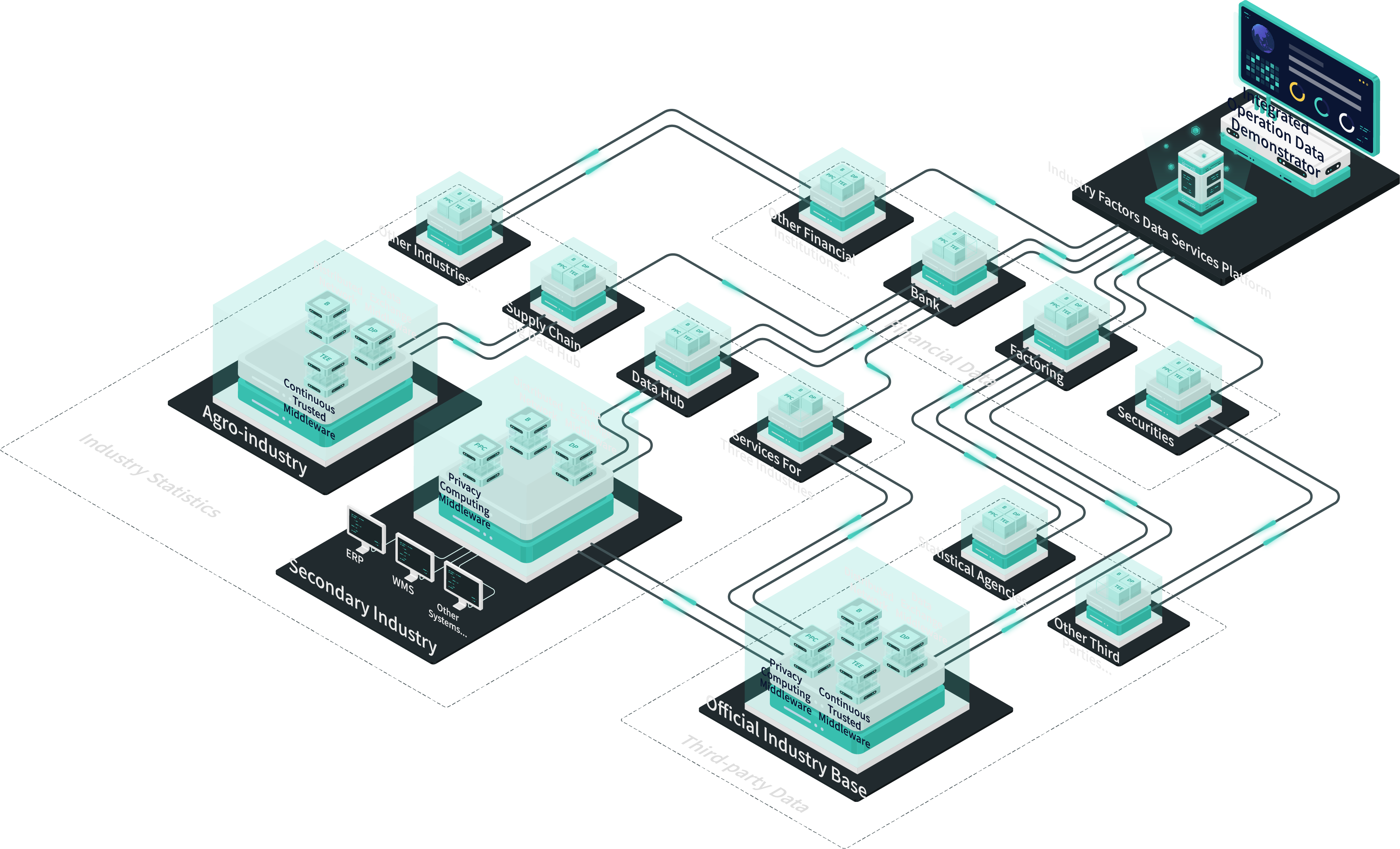
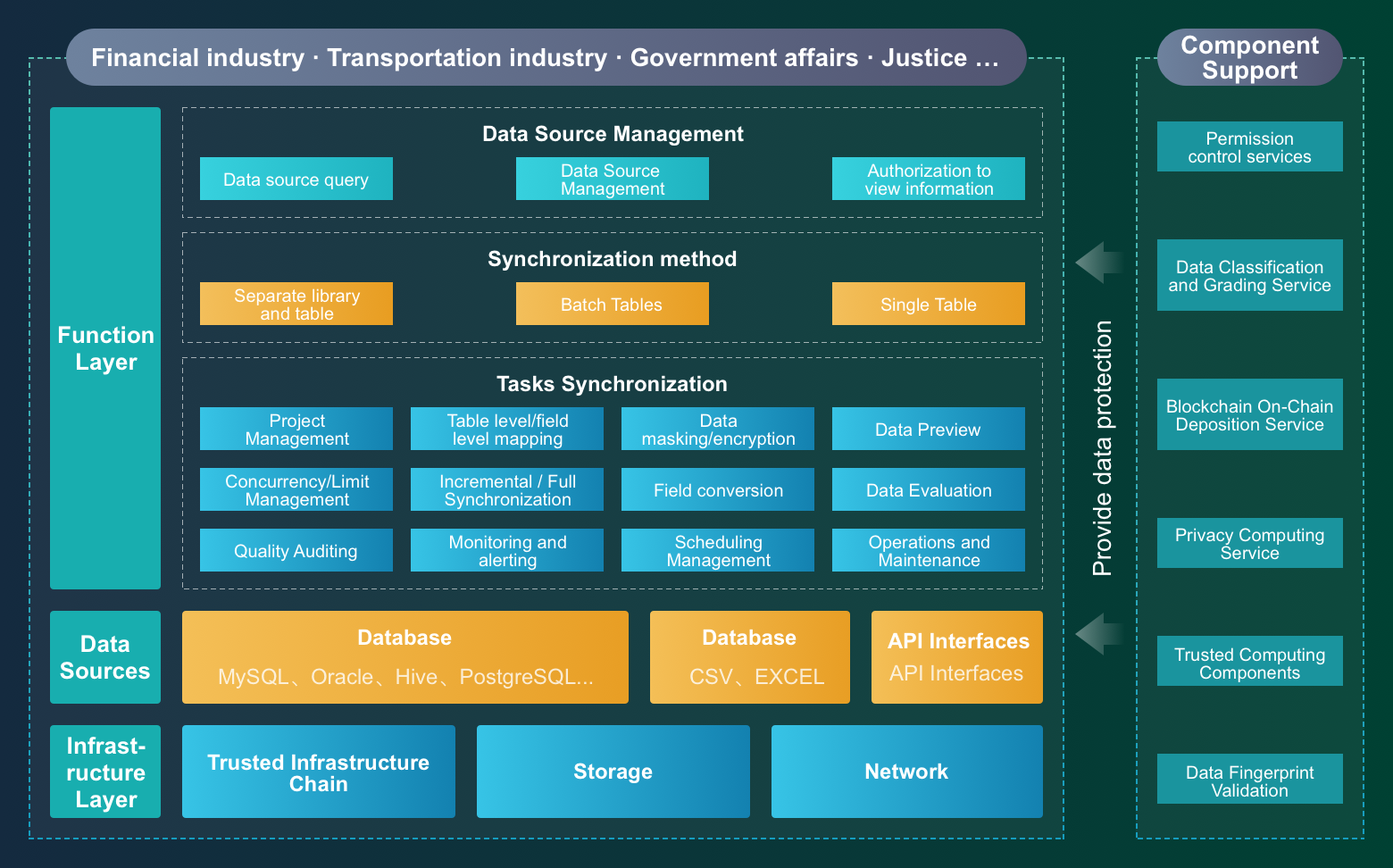
Data Exchange
1. Use real-name authentication + on-chain identity + identity verification to achieve a credible identity.
2. Realize efficient access to multi-source heterogeneous data with visual configuration.
3. Use the tamper-proof and traceable features of blockchain technology to credibly register the whole process of data circulation, which is convenient for regulators to audit and ensure trusted data circulation.
4. Ensure the consistency and integrity of data at both ends of transmission through data fingerprinting.
5. Data security technologies such as end-level encryption and decryption, static data masking, and privacy calculation are used to achieve privacy and security compliance of data transmission.
Privacy Computing
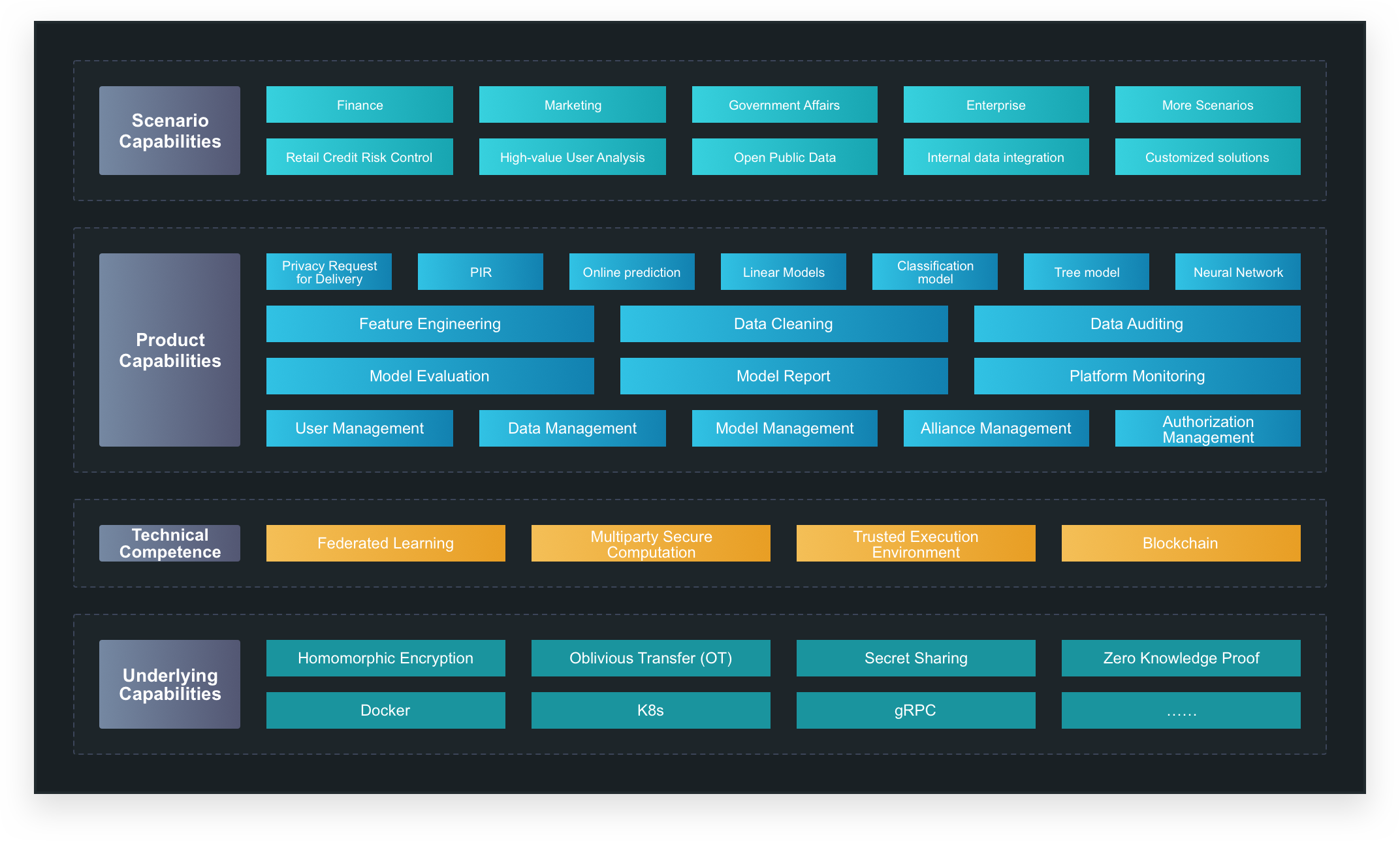
01.
Data security
Industrial element data, as a production factor, needs to be released in value under the condition of securing its assets.
02.
Privacy computing
Applying cryptographic techniques such as homomorphic encryption and oblivious transfer, ciphertext interaction, no exposure of plaintext information, and irreversible ciphertext of interaction.
03.
Value circulation
Adopt privacy computing technology to realize the usable invisibility and usable measurability of data and release the value of industrial data.
04.
Autonomous and controllable
Adopt privacy computing technology to realize the usable invisible and usable measurable data, and release the value of industrial data.
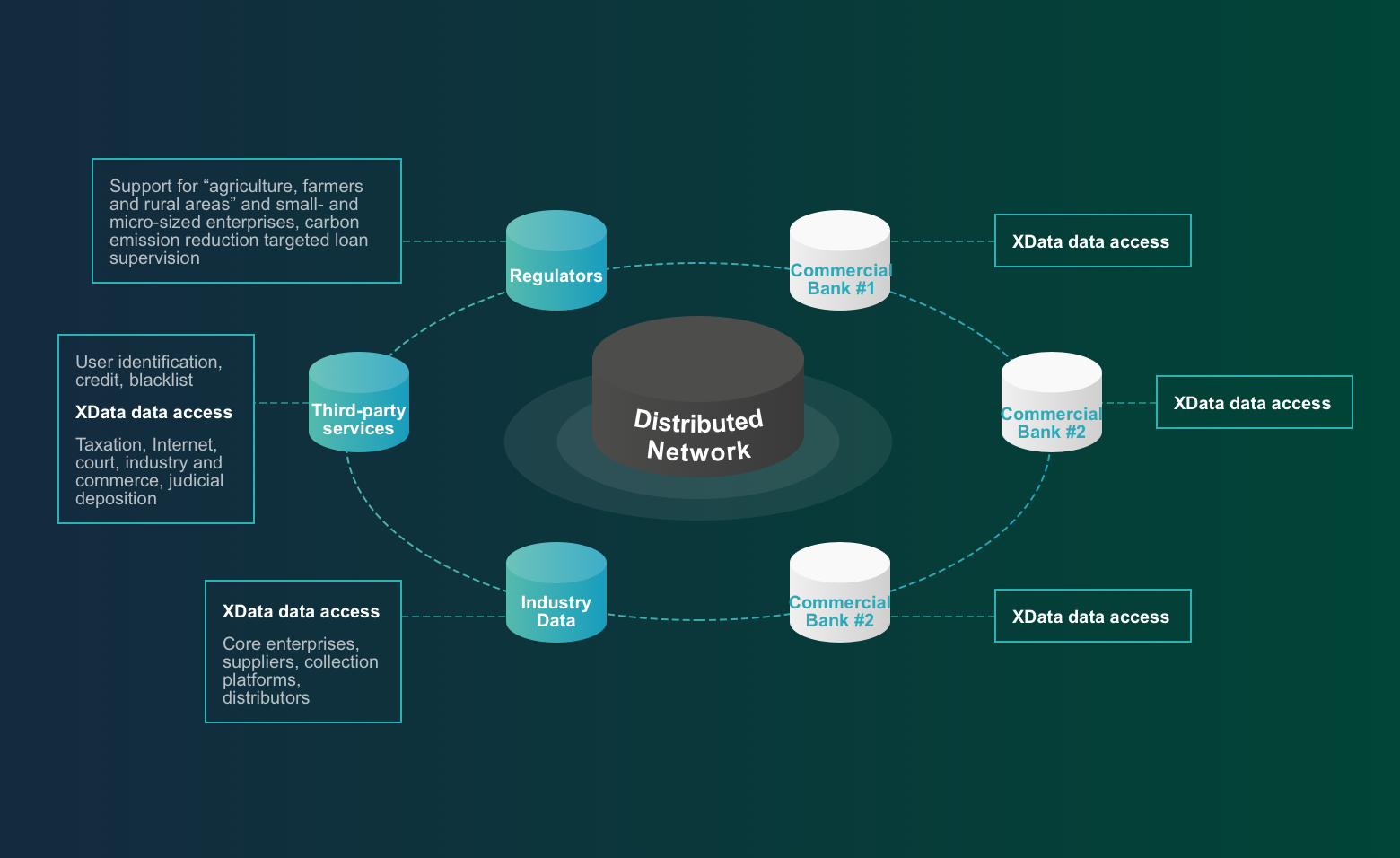
Distributed Network
Blockchain technology is used to deploy blockchain nodes in important data hubs to form a distributed network and construct a trusted data base.
Taking the regulatory perspective of the People's Bank of China as an example, distributed nodes can be deployed at multiple nodes of the People's Bank of China, city commercial banks, core enterprises at the industrial end, industrial platforms, industry and commerce, taxation, etc. to realize a distributed financial regulatory network and ensure trusted data circulation through consensus mechanisms among nodes.